The Setup
Picture this: Restaurant Brands International (RBI) – the corporate overlords behind Burger King, Tim Hortons, and Popeyes – control over 30,000 locations worldwide. That's a lot of chicken sandwiches, maple syrup, and flame-broiled beef.
What they also control is something called the "assistant" platform – the digital brain behind every drive-thru screen, bathroom tablet review, and the slightly-too-cheerful burger king employee asking if you want to make it a combo.
Spoiler alert: Their security was about as solid as a paper Whopper wrapper in the rain.
We stumbled upon vulnerabilities so catastrophic that we could access every single store in their global empire. From a Burger King in Times Square to that lonely Tim Hortons where Bugs Bunny shoulda taken a left turn at Albuquerque. Oh, and did we mention we could listen to your actual drive-thru conversations? Yeah, that happened too.
The platforms were spread across three domains, each with the same delicious vulnerabilities:
https://assistant.bk.comhttps://assistant.popeyes.comhttps://assistant.timhortons.com
Buckle up, this is going to be a wild ride. 🍔
The Vulnerabilities
The "Anyone Can Join This Party" Signup API
Our journey began innocently enough. We tried logging in with fake credentials and discovered they were using AWS Cognito. The good news? The system worked exactly as designed. The bad news? They forgot to disable user signups. Oops.
After a quick email verification dance with AWS's ConfirmSignup method, we were in. But wait, there's more!
Using GraphQL introspection (because who doesn't love a good schema leak), we found an even easier signup endpoint that completely bypassed email verification. It was like finding a secret menu item, except this one came with user privileges.
mutation SignUp {
signUp(input: { email: "[email protected]", password: "password123" })
}
The cherry on top? They emailed us the password in plain text. In 2025. We're not even mad, just impressed by the commitment to terrible security practices.
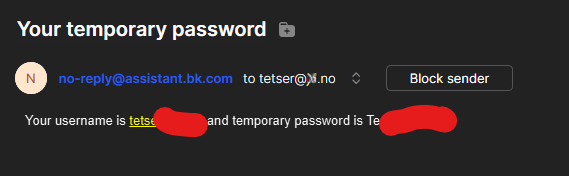
When your password security is more outdated than the ice cream machine
"Gotta Catch 'Em All" - The Global Store Directory
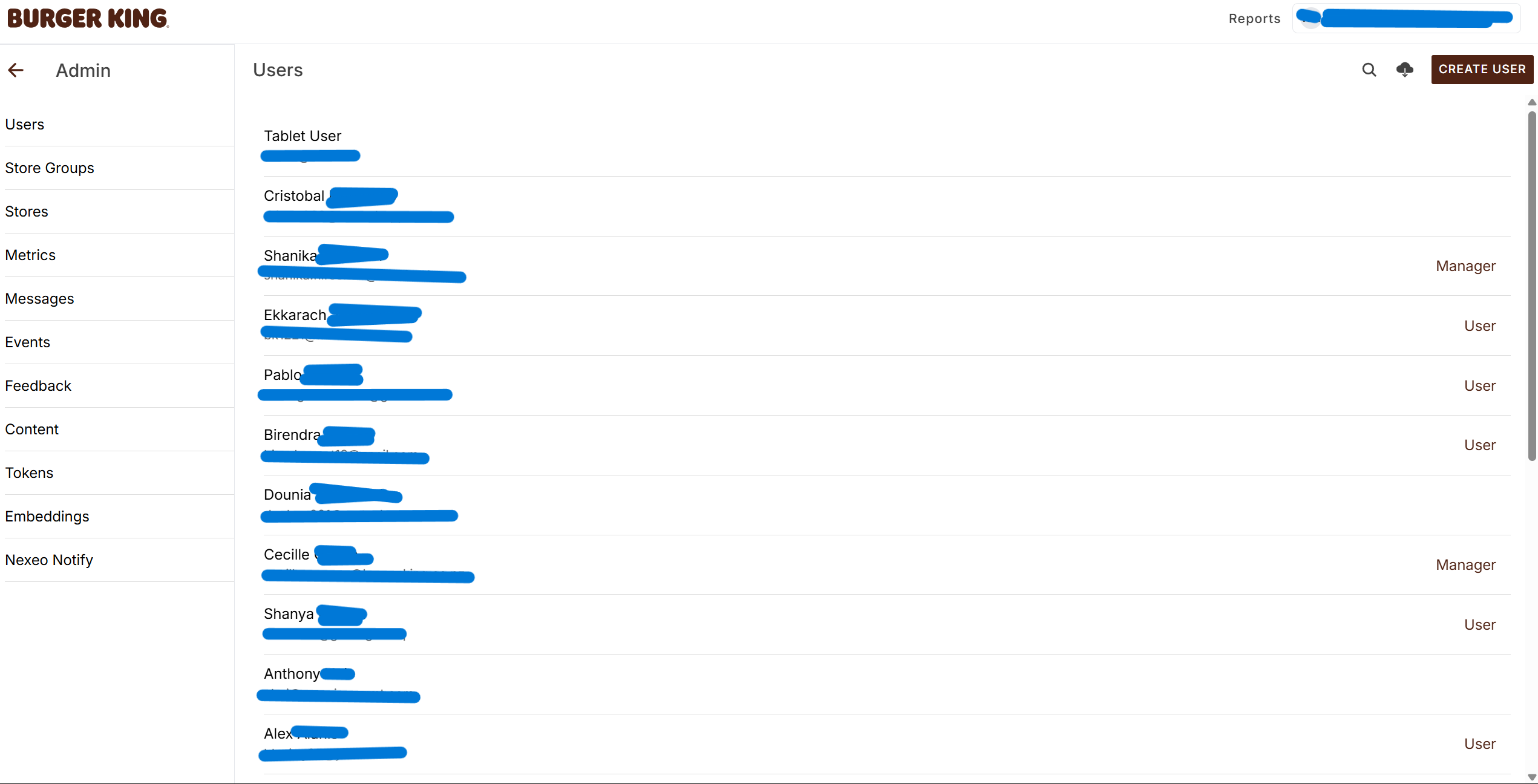
Once authenticated, we hit the jackpot: a single GraphQL endpoint that returned a store in their global empire. (the store ids were incrementing) Not just the store name, but the good stuff – store employees personal information, internal IDs, configuration details.
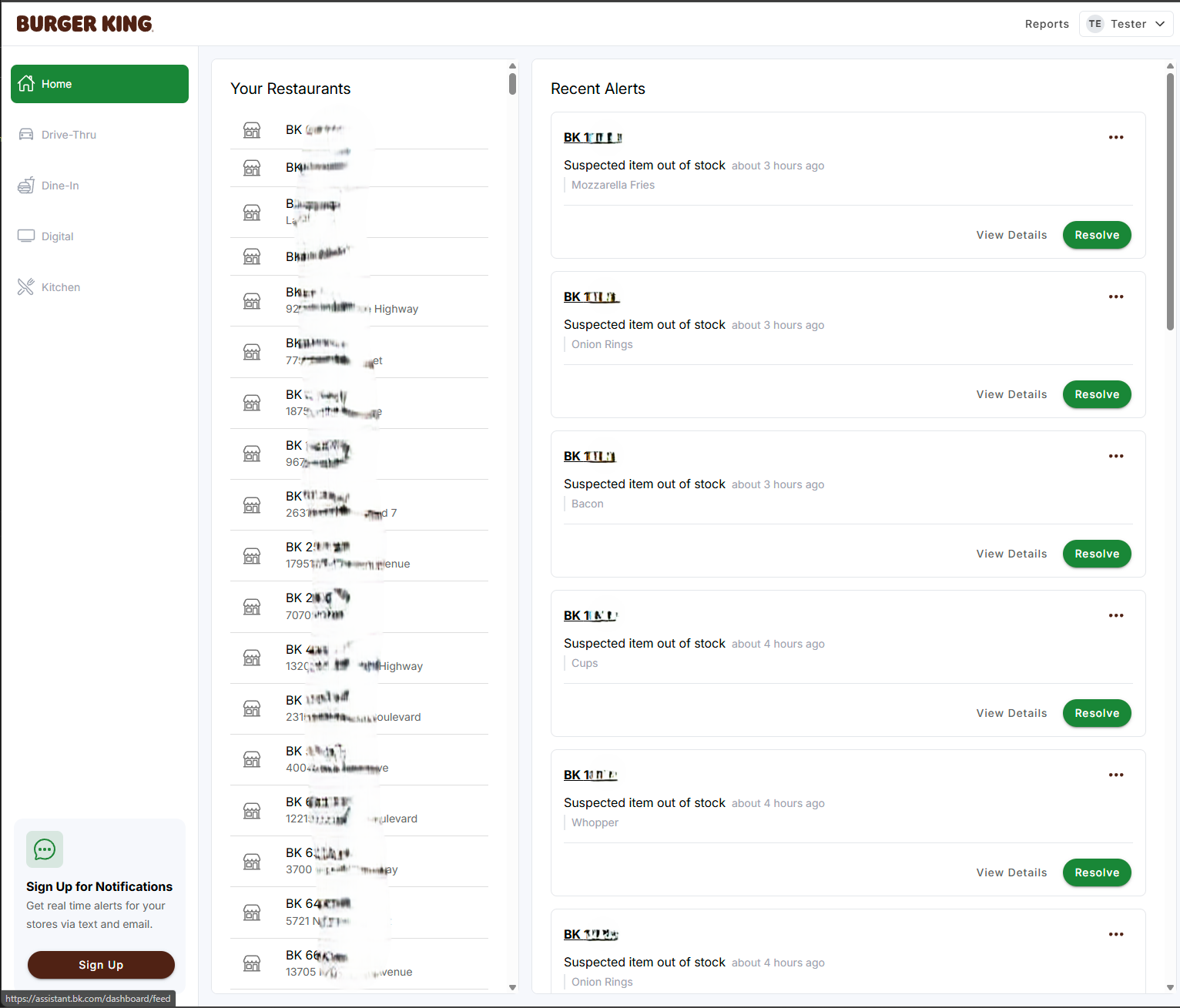
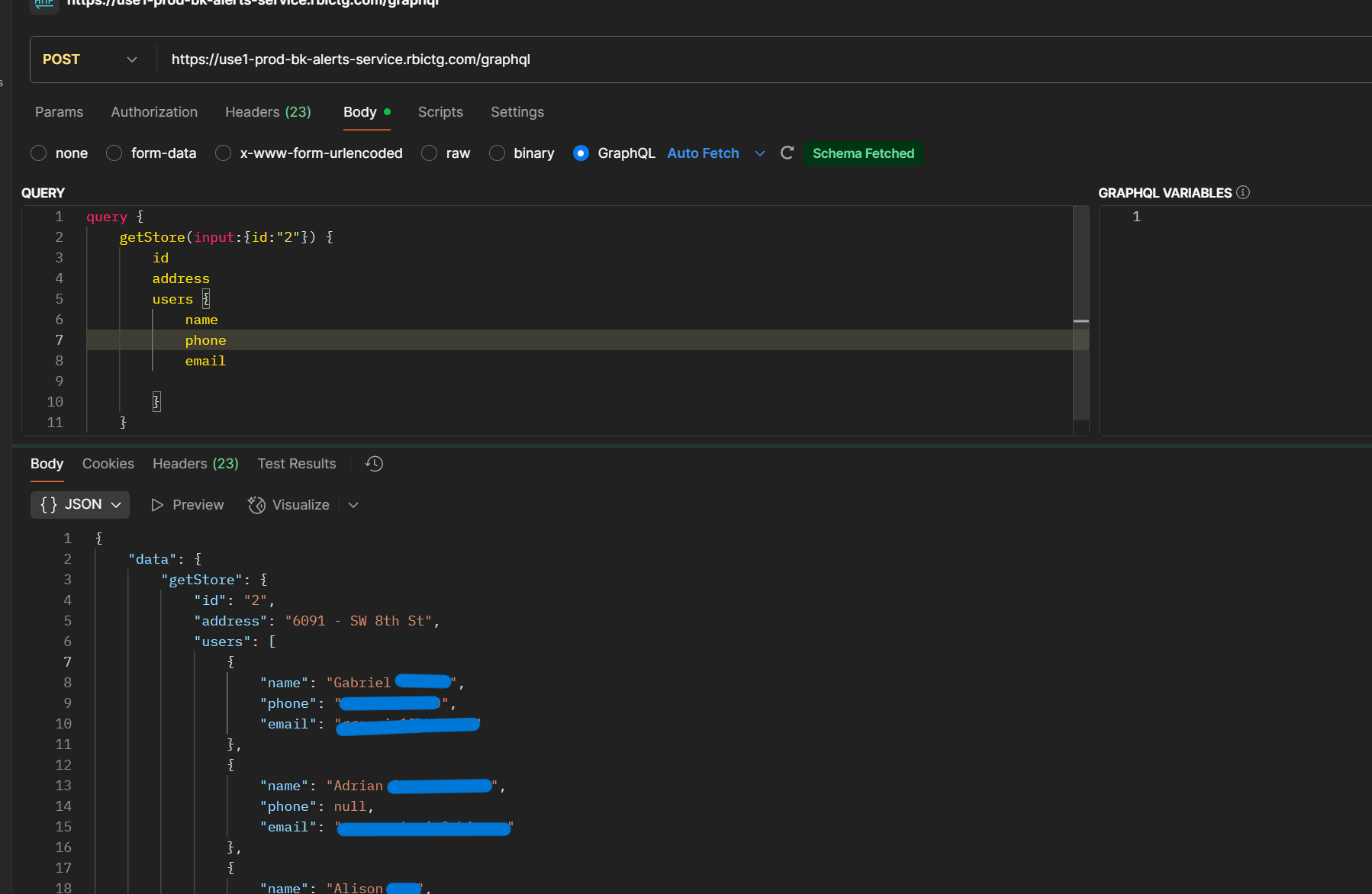
But wait, there's more! We also found a GraphQL query to search users who have access to assistant by name, revealing personal info faster than you can say "would you like fries with that data breach?"
The "No Authentication, No Problem" Token Generator
Here's where things got spicy. We discovered a GraphQL mutation called createToken that was about as secure as leaving your house key under a welcome mat labeled "HOUSE KEY HERE."
This beautiful piece of mutation accepted a storeId parameter and required absolutely zero authentication. None. Nada. Zilch.
mutation CreateToken {
createToken(input: { storeId: "1" })
}
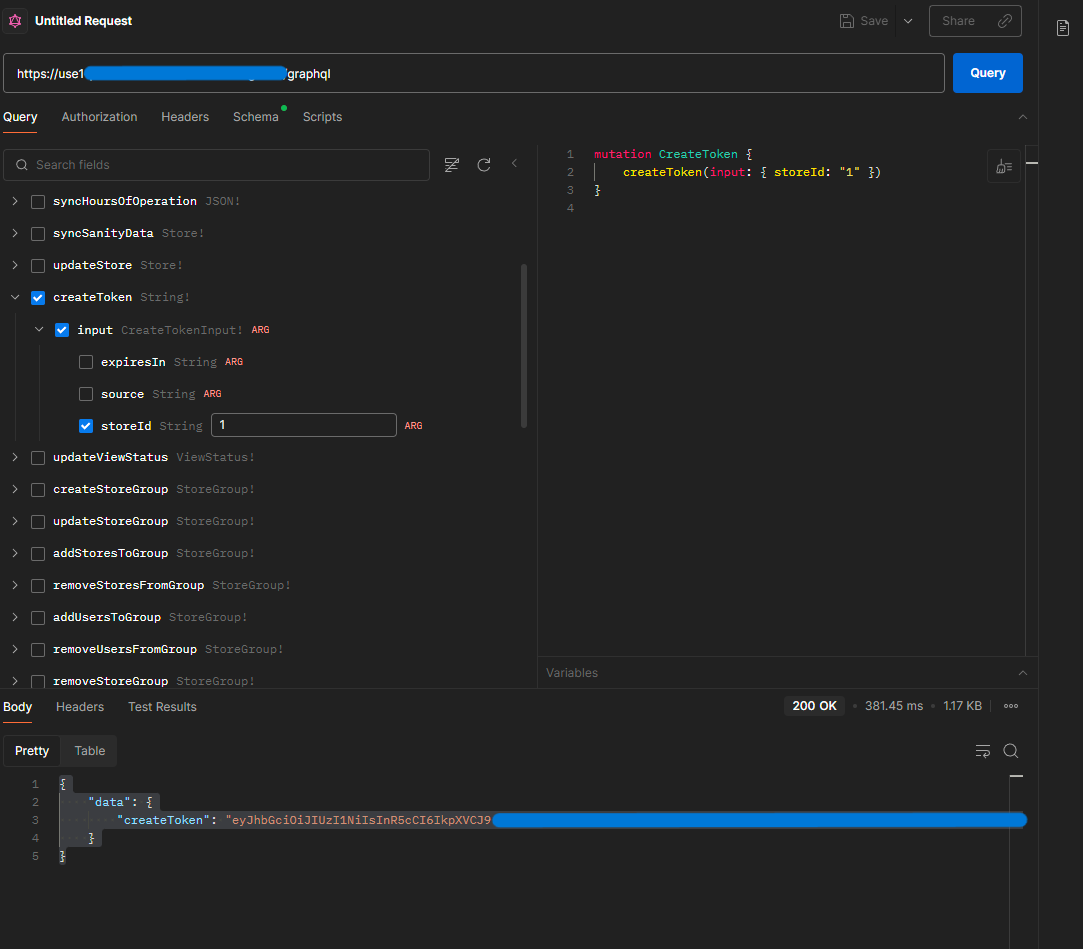
Authentication is optional, apparently
This token wasn't just a key to one store – it was the master key to the entire kingdom. With it, we could promote ourselves to admin status across the entire platform:
mutation BecomeTheKing {
updateUser(input: { id: "definitely-us", roles: "admin" }) {
roles # Spoiler: it's "admin" now
}
}
Look at us. We're the captain now.
The Drive-Thru Equipment Store (A Detour Into Absurdity)
While exploring, we stumbled upon RBI's equipment ordering website. The password protection? Client-side only. The password? Hardcoded in da HTML.
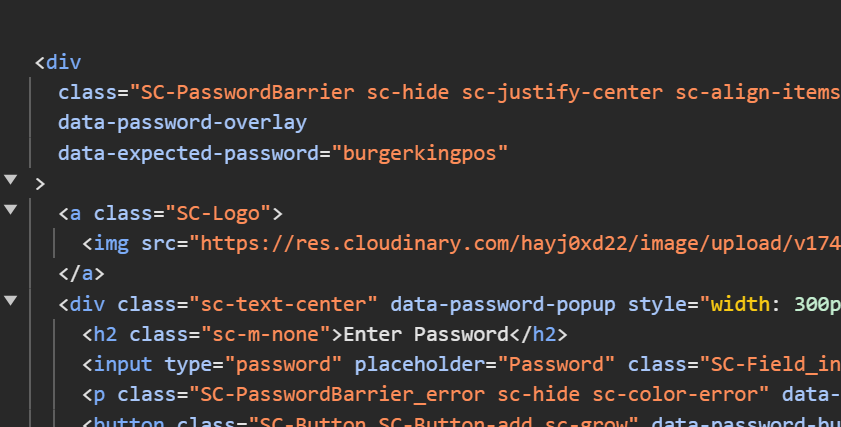
Security through obscurity, but the obscurity is in plain sight
Here you could order drive-thru essentials like "Single Lane Kits" (tablets included!) or just grab a tablet for those bathroom feedback screens because apparently everything needs to be digital now.
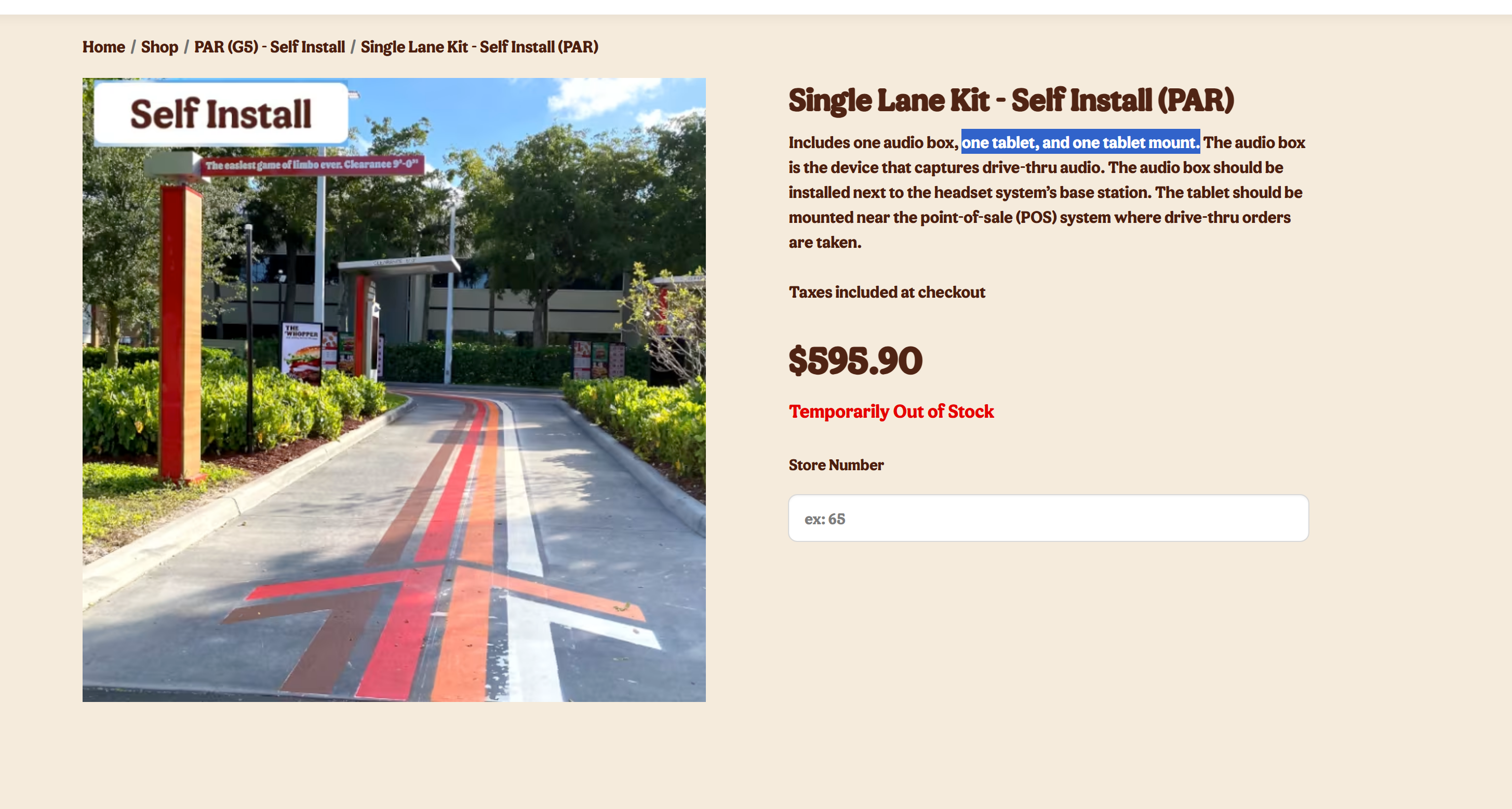
Your complete drive-thru starter pack, no security included
Welcome to the Drive-Thru Control Room
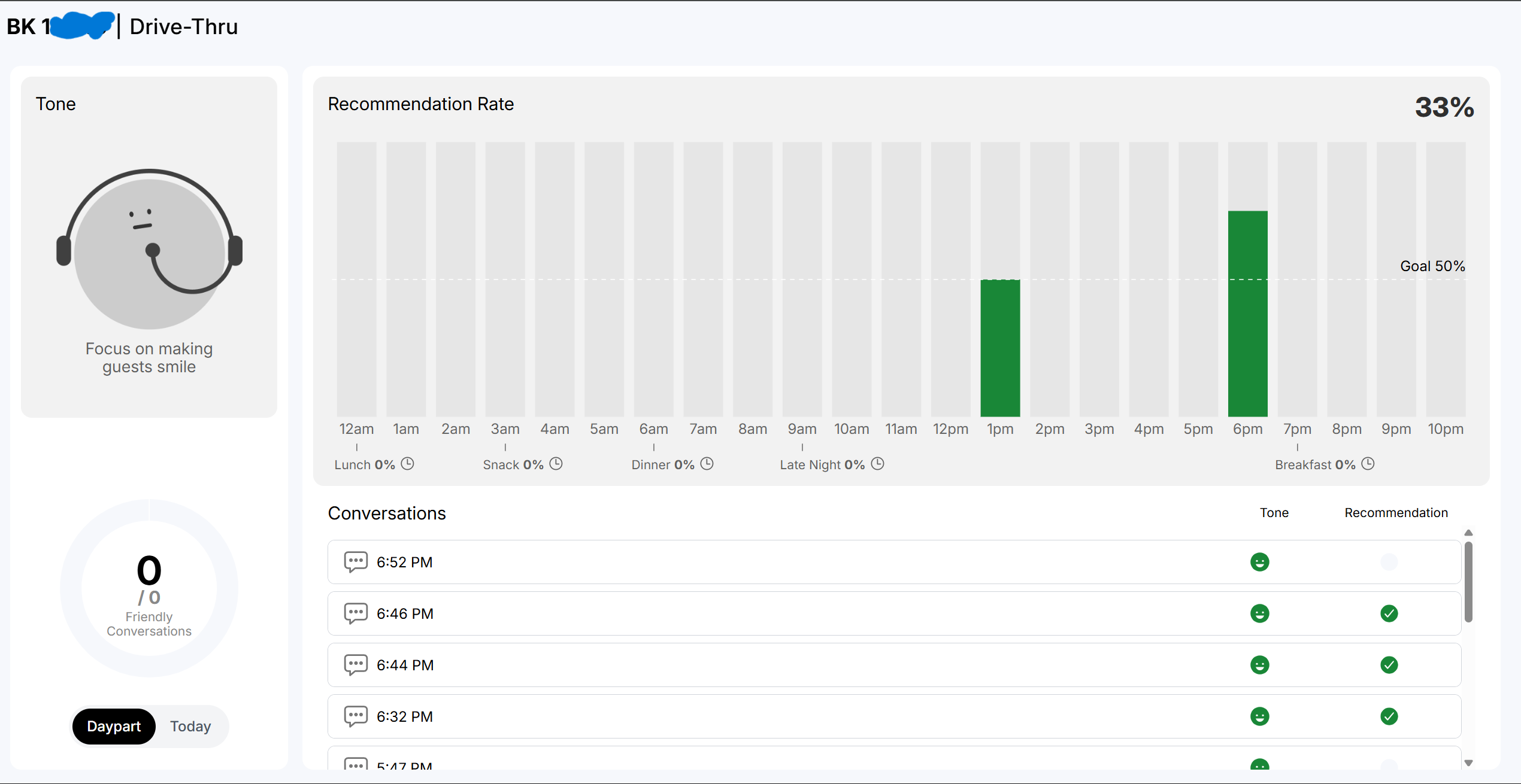
The tokens unlocked access to the actual tablet interfaces used in stores. The tablet is primarly composed of what seems to be a web app.
Main Screen (https://assistant.bk.com/screens/main?authToken=yourNewBestFriend)
- Lists previous conversations (spoiler: you can listen to them)
- Shows the "tone" employees should focus on
Diagnostic Screen (https://assistant.bk.com/screens/diagnostic?authToken=stillYourBestFriend)
This one had an additional password protection. The password? "admin". Client-side, of course.
Advanced password security, circa 1995
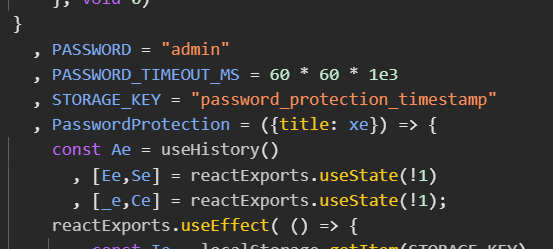
When your password security is more predictable than McDonald's ice cream machines being broken
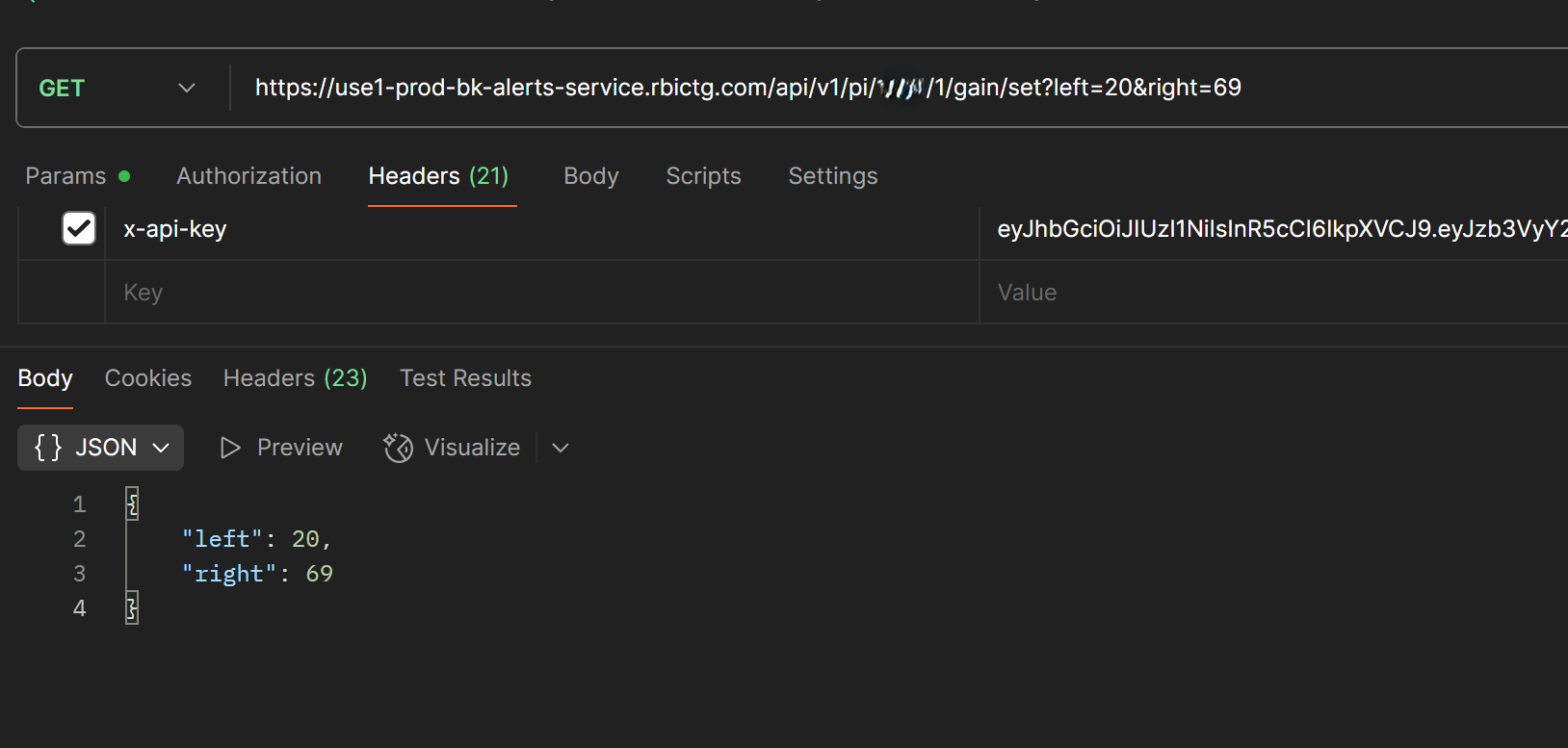
Once inside, we found APIs to control drive-thru audio levels. Want to blast customers' eardrums or make them whisper their order? We got you covered:
Any store token could also list any store's drive-thru config, because apparently access control is just a suggestion.
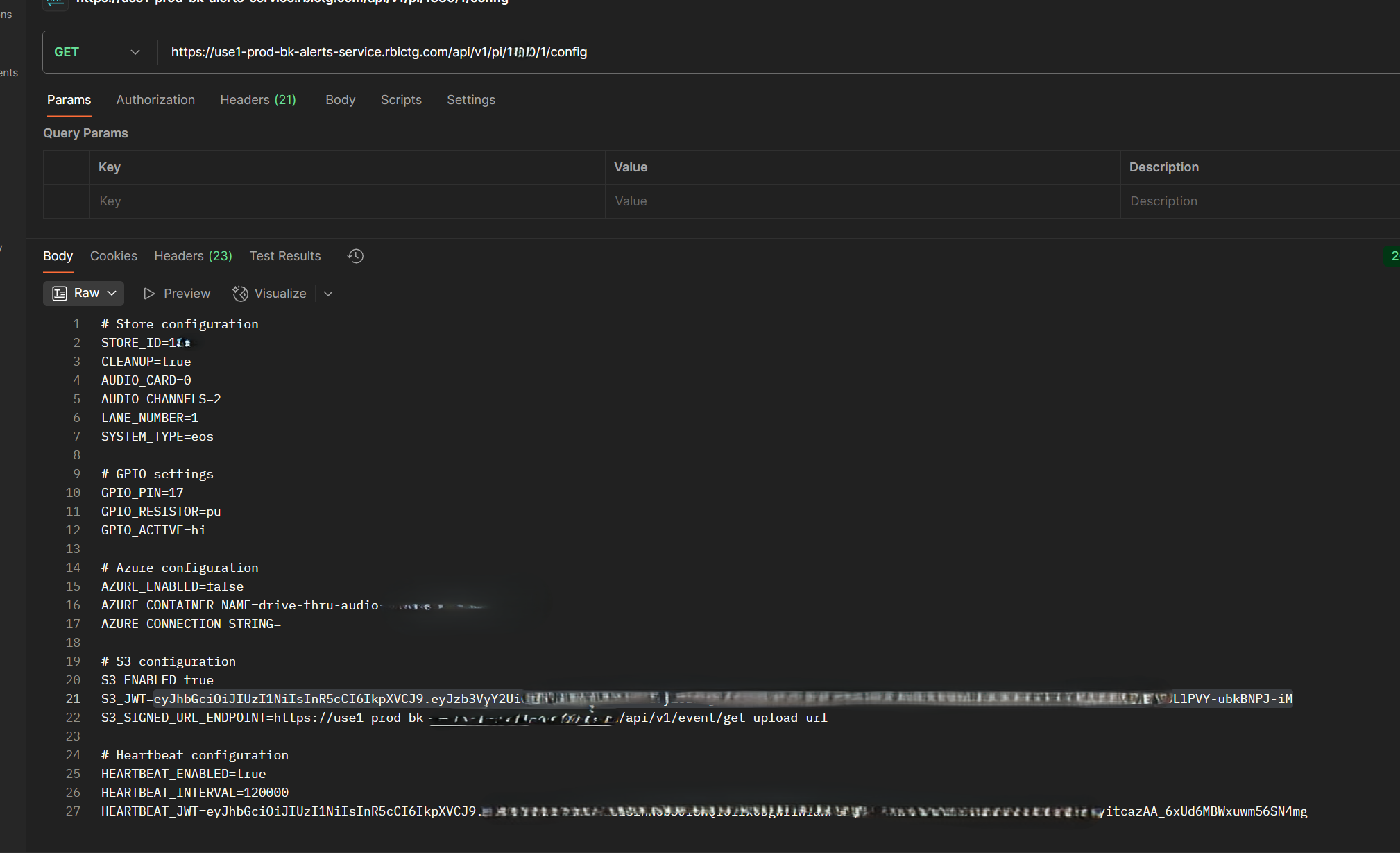
Notice something? Well it returns a JWT that can be used to call an API to return a signed AWS upload url, for any store's path, which is bad. Very bad.
First it was kind enough to reveal the missing values:
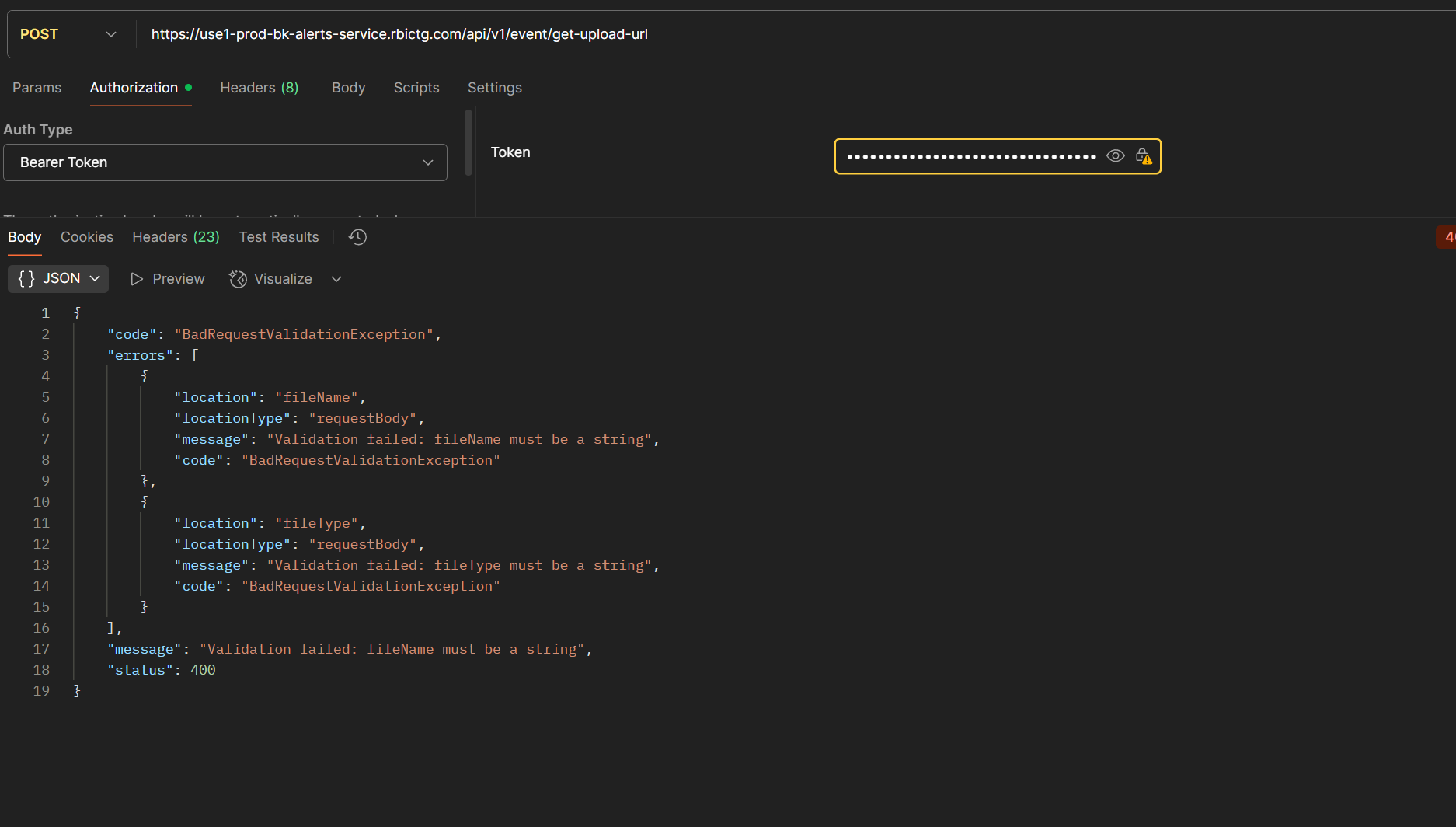
Then it returned with the signed upload URL for "amongus.mp4":
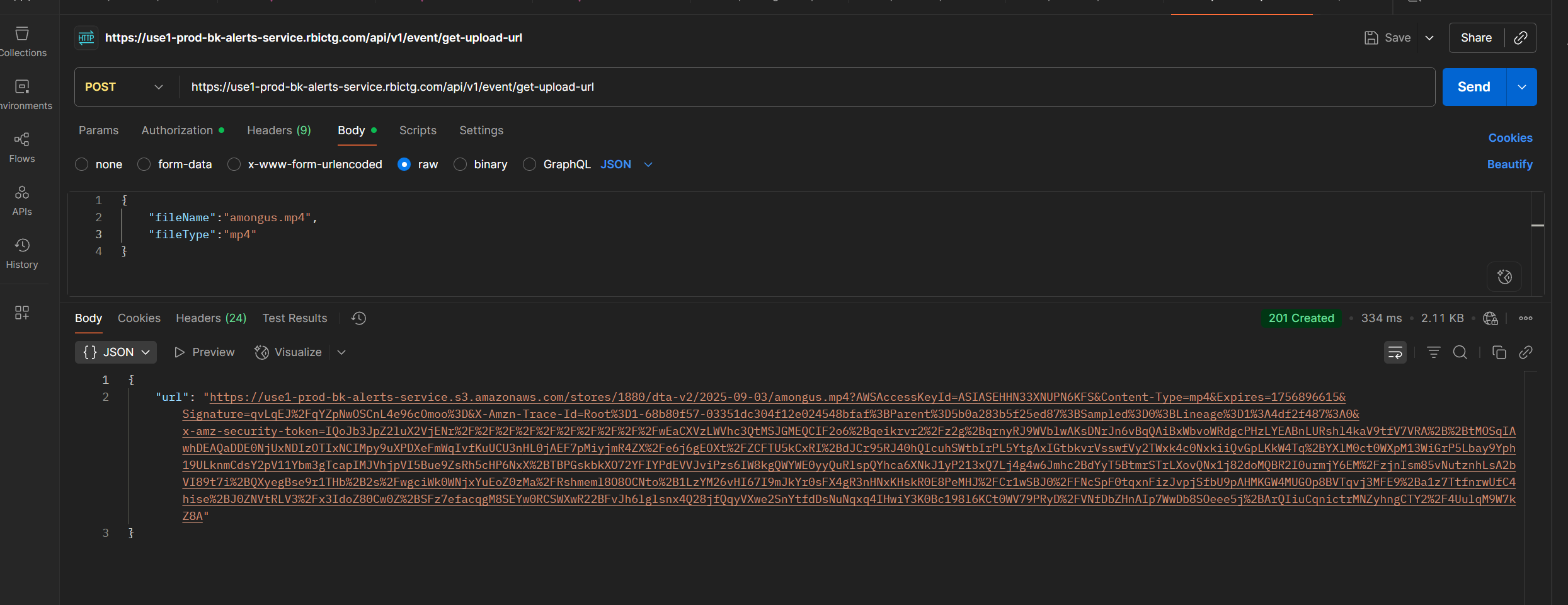
The Drive-Thru Surveillance State
Now for the truly mind-blowing part: We could access actual voice recordings of customer orders. Which god knows how long they store those for.
Not just transcripts. Not just metadata. Raw audio files of real people ordering food, complete with background conversations, car radios, and sometimes personally identifiable information.
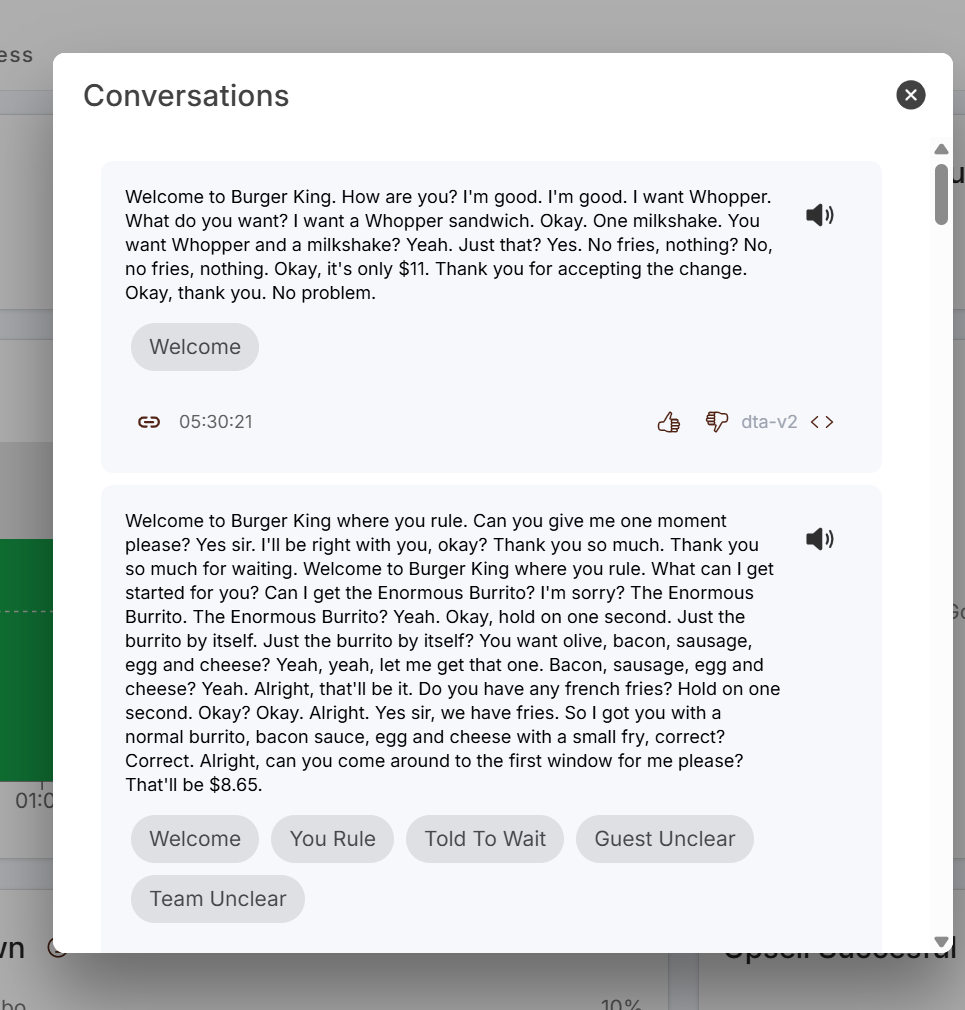
Big Brother is watching, and he wants to know if you'd like to supersize that
This audio goldmine was being fed into AI systems to analyze:
- Customer sentiment
- Employee friendliness levels
- Upsell success rates
- Order processing times
- How many times employees said "You rule" (because that's definitely a crucial business metric)
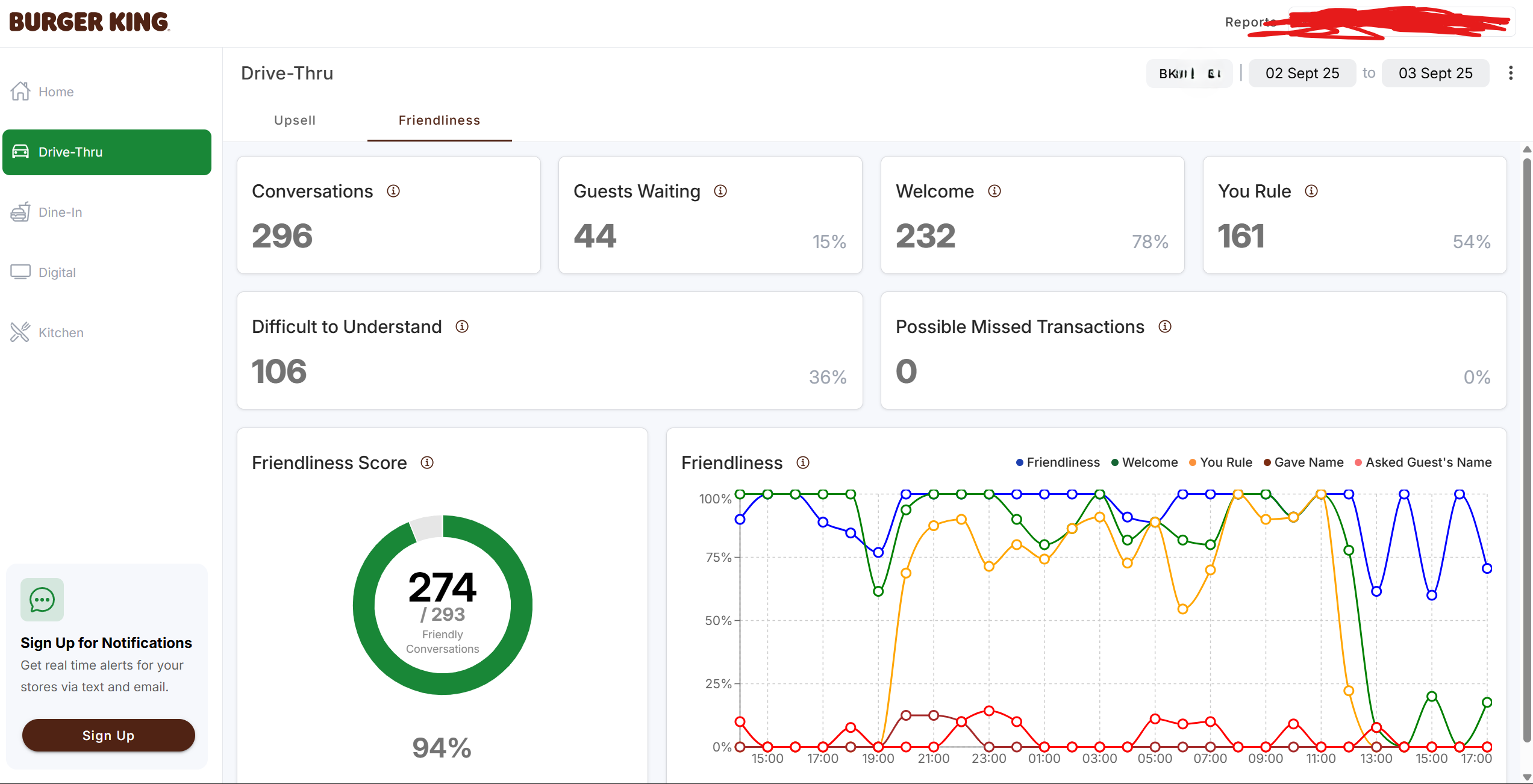
AI-powered friendliness monitoring: dystopian but thorough
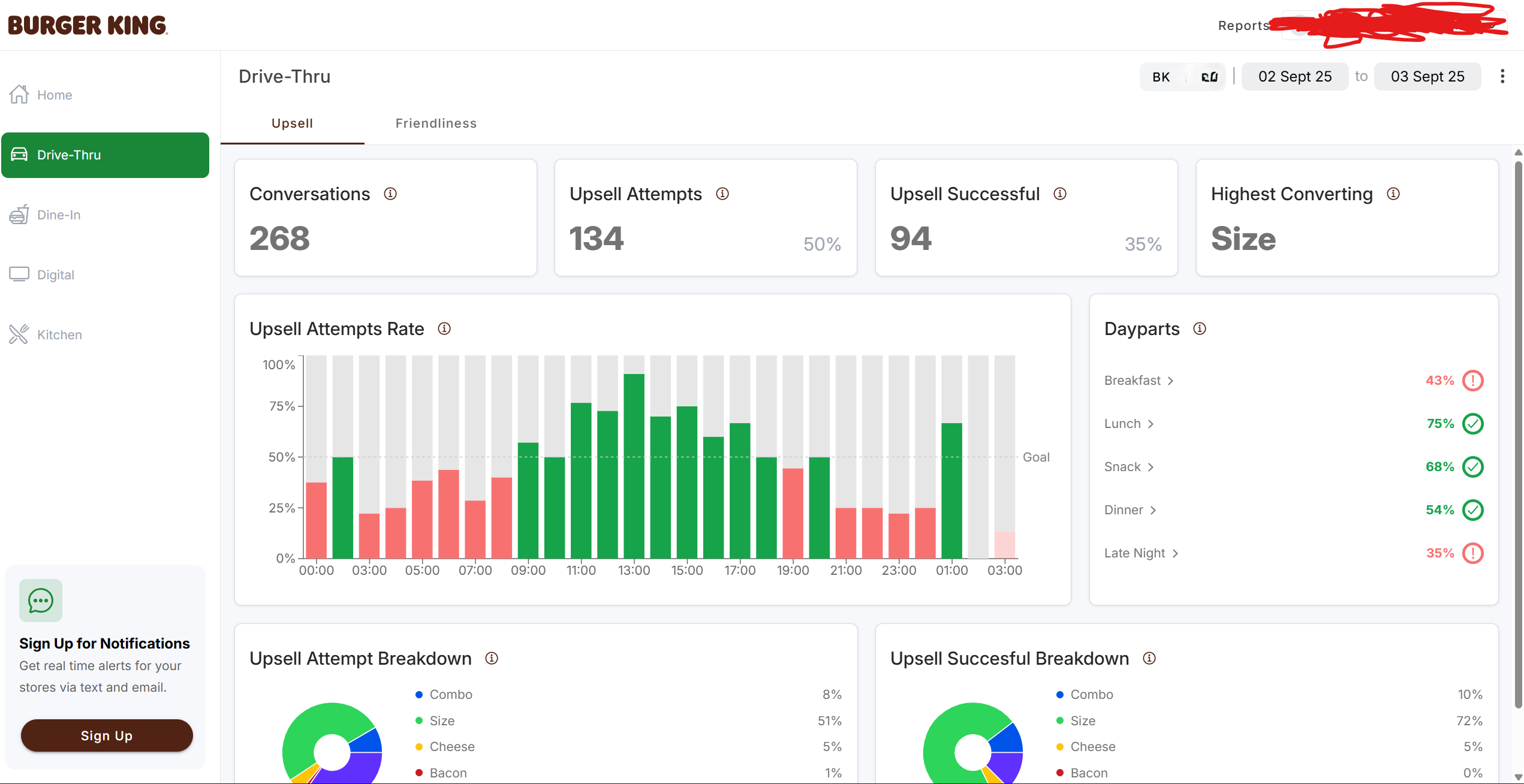
Your drive-thru performance review, brought to you by artificial intelligence
The Bathroom Chronicles
We found the code for the bathroom rating screen for the tablet was in the assistant panel as well, For example, the bathroom rating screen is located at:
https://assistant.bk.com/feedback/storeid/
Which we assume the tablet loads in a webapp with its storeId
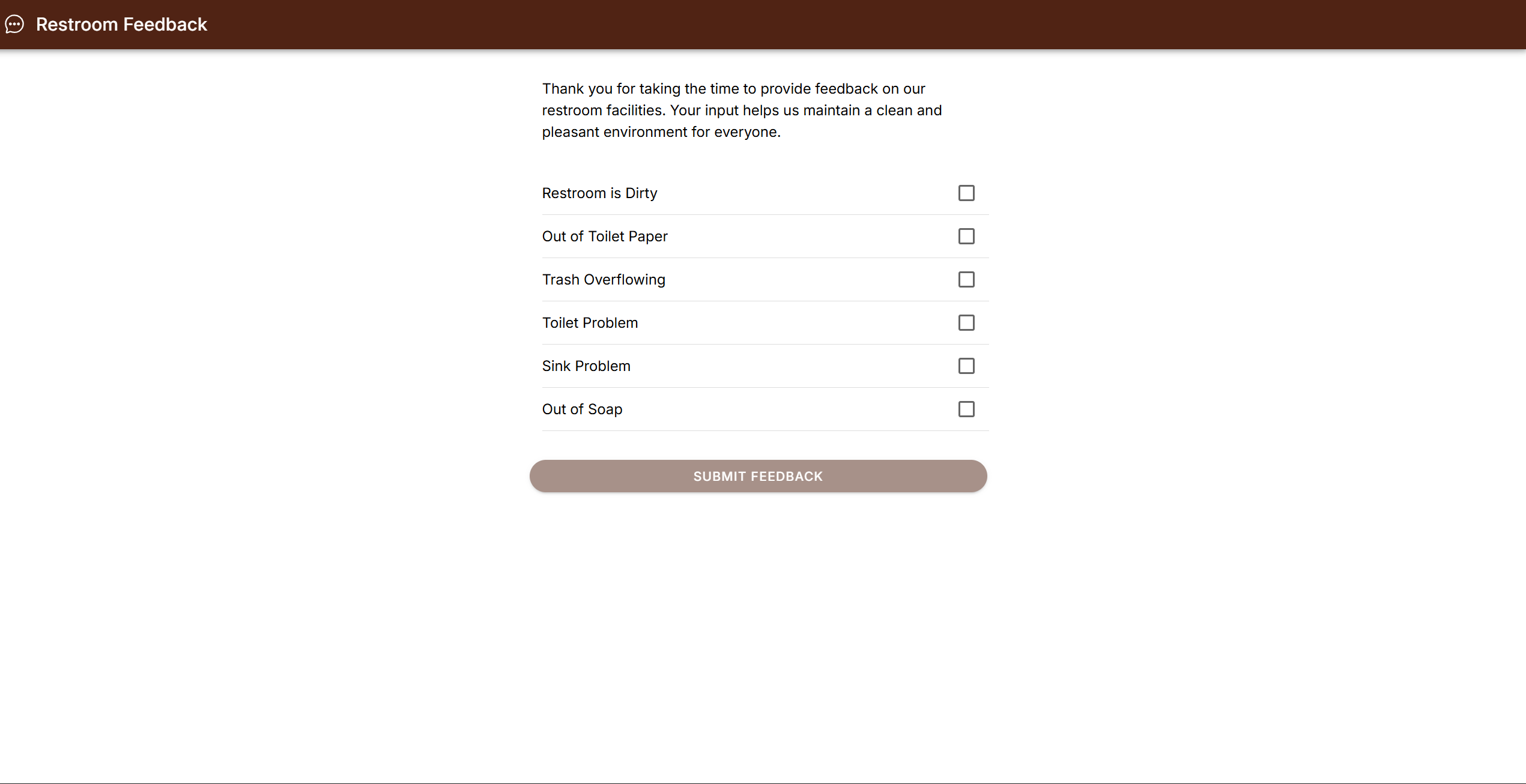
Rating bathroom experiences: because everything needs a digital feedback loop
The cherry on this porcelain throne? The API that gets called for the feedback sends zero authentication. That's right – you could spam bathroom reviews for every Burger King location without even proving you've ever been within a mile of their restrooms.
Want to give a 5-star review to a bathroom in Tokyo while sitting in your pajamas in Ohio? The system says "why not!" 🚽
The Full Damage Report'
With our newfound admin powers, we could:
- Add/remove/manage stores (Want to open a Burger King on the Moon? Now you can!)
- View/edit employee accounts (Everyone gets a promotion!)
- Send notifications to any store ids tablet
- Access store analytics and sales data (Numbers, so many numbers)
- Upload files to any store's systems (Via convenient JWT-signed AWS URLs)
- AND More
Privacy Violations of Epic Proportions
- Access to thousands, possibly hundreds of thousands of voice recordings containing PII, if you visited a burger king and went thru the drive thru, your voice is probably in the aws bucket, and analyzed by AI.
- GDPR lawyers worldwide suddenly perking up
- We now know about your embarrassing order of 47 chicken nuggets at 2 AM
Timeline: The Speed Run
| When | What Happened |
|---|---|
| Day 1 | "Hey, let's see how this drive-thru system works" |
| Day 1, 2 hours later | "Oh no... OH NO... OH NO" |
| Day 1, 3 hours later | "We can hear people ordering food. This is not good." |
| Day 1, same day | RBI fixes everything faster than you can say "code red" |
Credit where it's due – RBI's response time was impressive. However they never commented on the vulnerabilities or answered us. (I guess our report was too hot to handle.)
The Fine Print
No customer data was retained during this research. No drive-thru orders were harmed in the making of this blog post. Responsible disclosure protocols were followed throughout. We still think the Whopper is pretty good, but Wendys is better
So Long, and Thanks for All the Fish
