The Energy Drink Giant That Forgot to Lock Its Doors
As a hacker who likes energy drinks, I decided to check out Monster Energy's corporate infrastructure. What I found was completely exposed and making terrible security decisions.
Monster University: Where Security Goes to Die
Monster University (mu.monsterenergy.com) is where Monster employees go to learn about their brand. It's also where I learned that changing /login to /register in the URL is apparently Monster's idea of "authentication."
The registration form appeared but wouldn't submit. So I went straight to the JavaScript to find the actual API endpoint. The API helpfully told me exactly which fields were missing from my registration attempt.
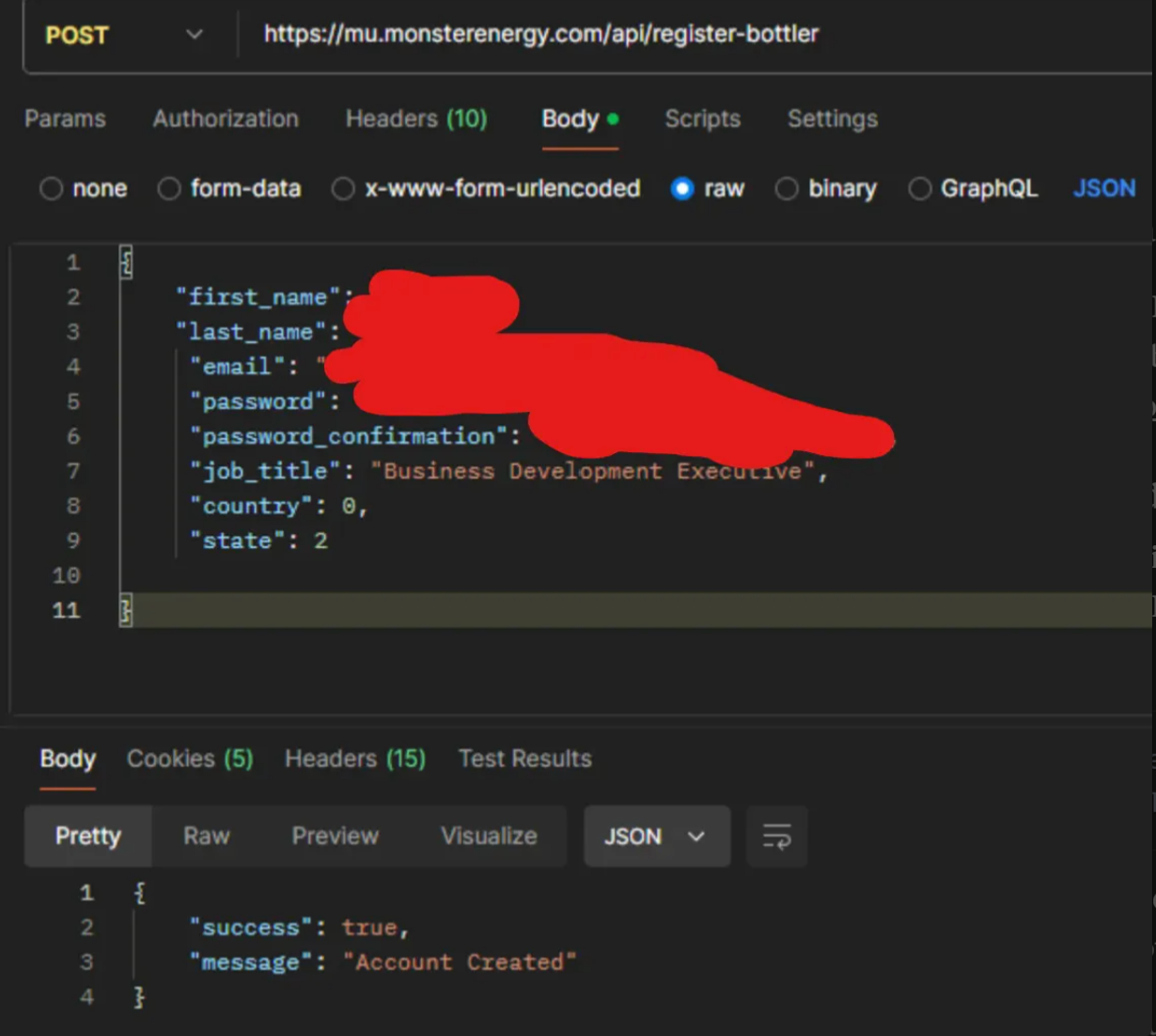
Once I called the API directly with the right fields, boom, I was in. Full access to Monster University, complete with all their training materials, including this absolute masterpiece about their target demographic:
This Is What Monster Thinks You Look Like
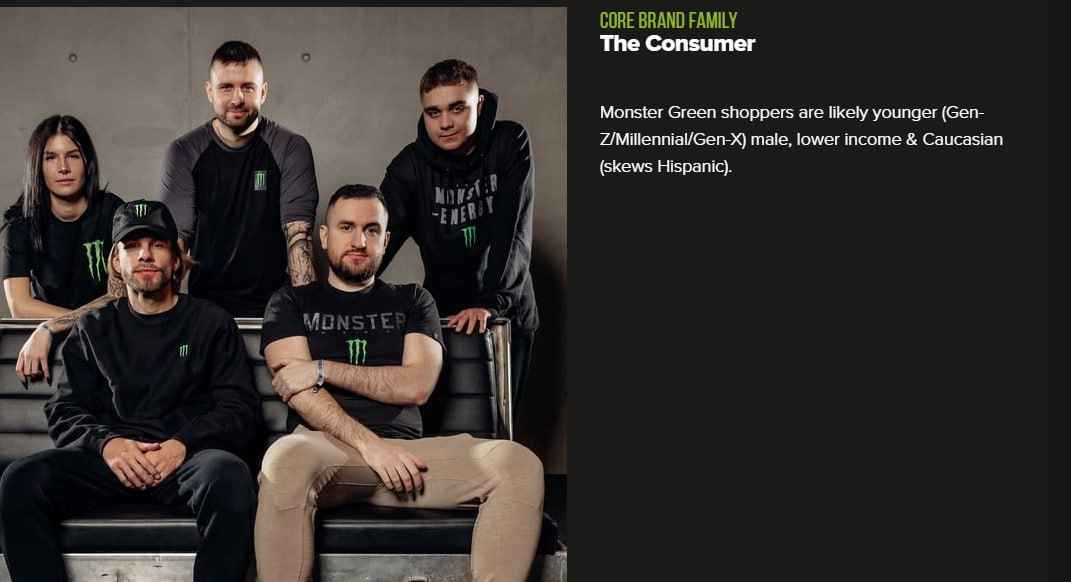
I'm not kidding. This is from their actual brand training guide. According to Monster Energy, their "Core Brand Family Consumer" is:
"Monster Green shoppers are likely younger (Gen-Z/Millennial/Gen-X) male, lower income & Caucasian (skews Hispanic)."
And they included this photo of five people in Monster gear looking like they're being held hostage in a marketing photoshoot. This is literally what Monster corporate thinks their average customer looks like. I can't make this stuff up.
The Irony: Their Own Cybersecurity Training
The best part? Monster University has a cybersecurity course they bought from a third-party vendor. The same platform with no authentication has lessons teaching employees about phishing and basic security:

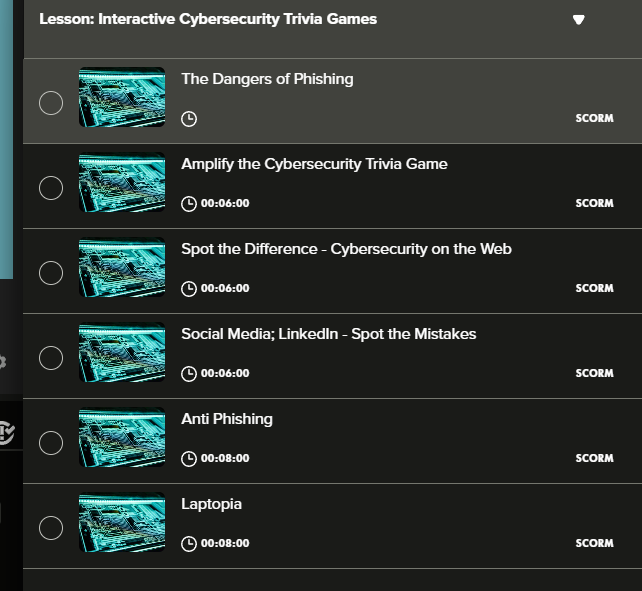
The irony of hosting a cybersecurity course about phishing on a completely unsecured platform is just chef's kiss.
Meanwhile in Monster Corporate: Walmart Zoom Calls and "ULTIMATE BEAST" Badges
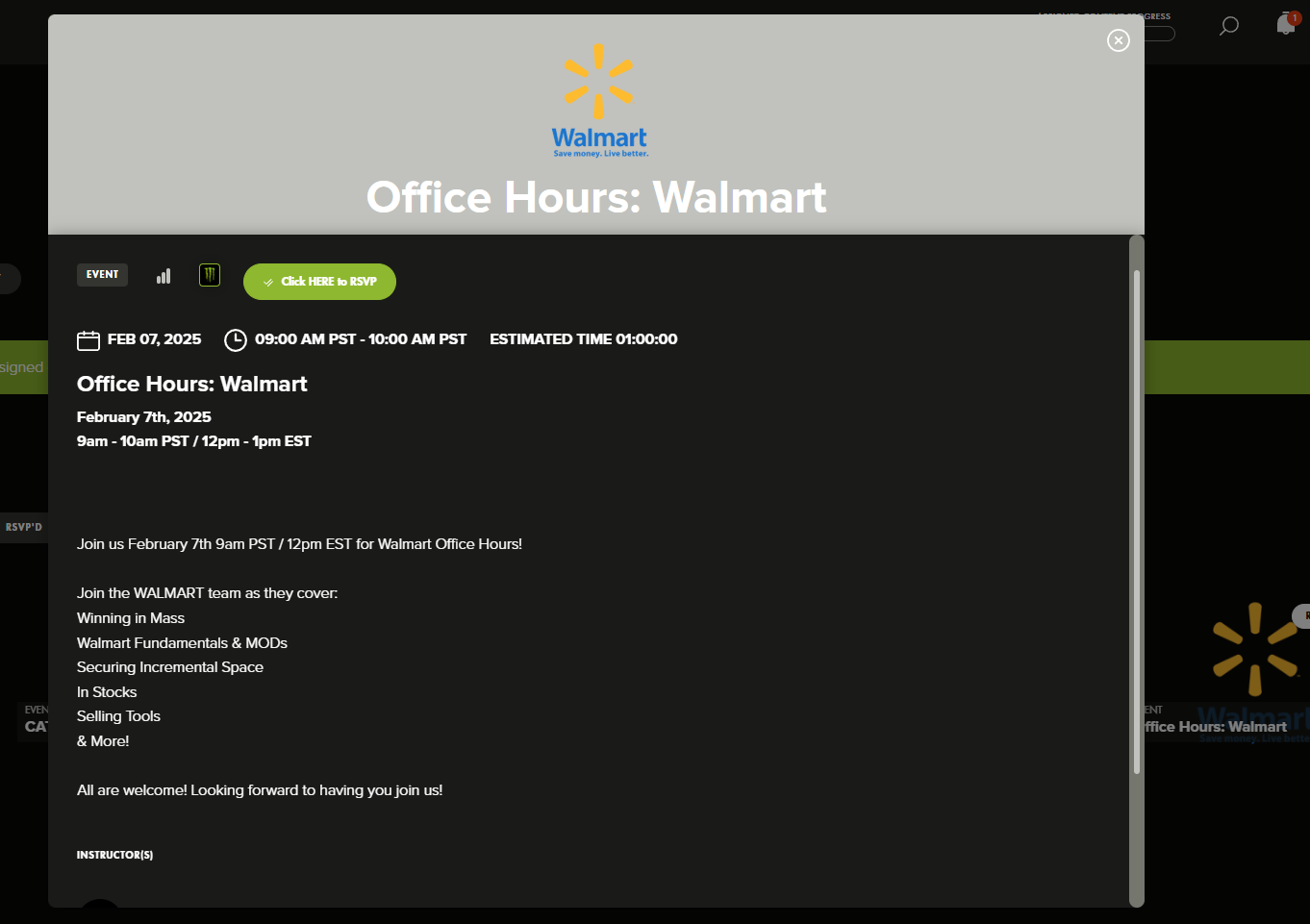
While exploring Monster University, I found some gems about their corporate culture. You can view their entire Zoom meeting schedule and even get the join links:
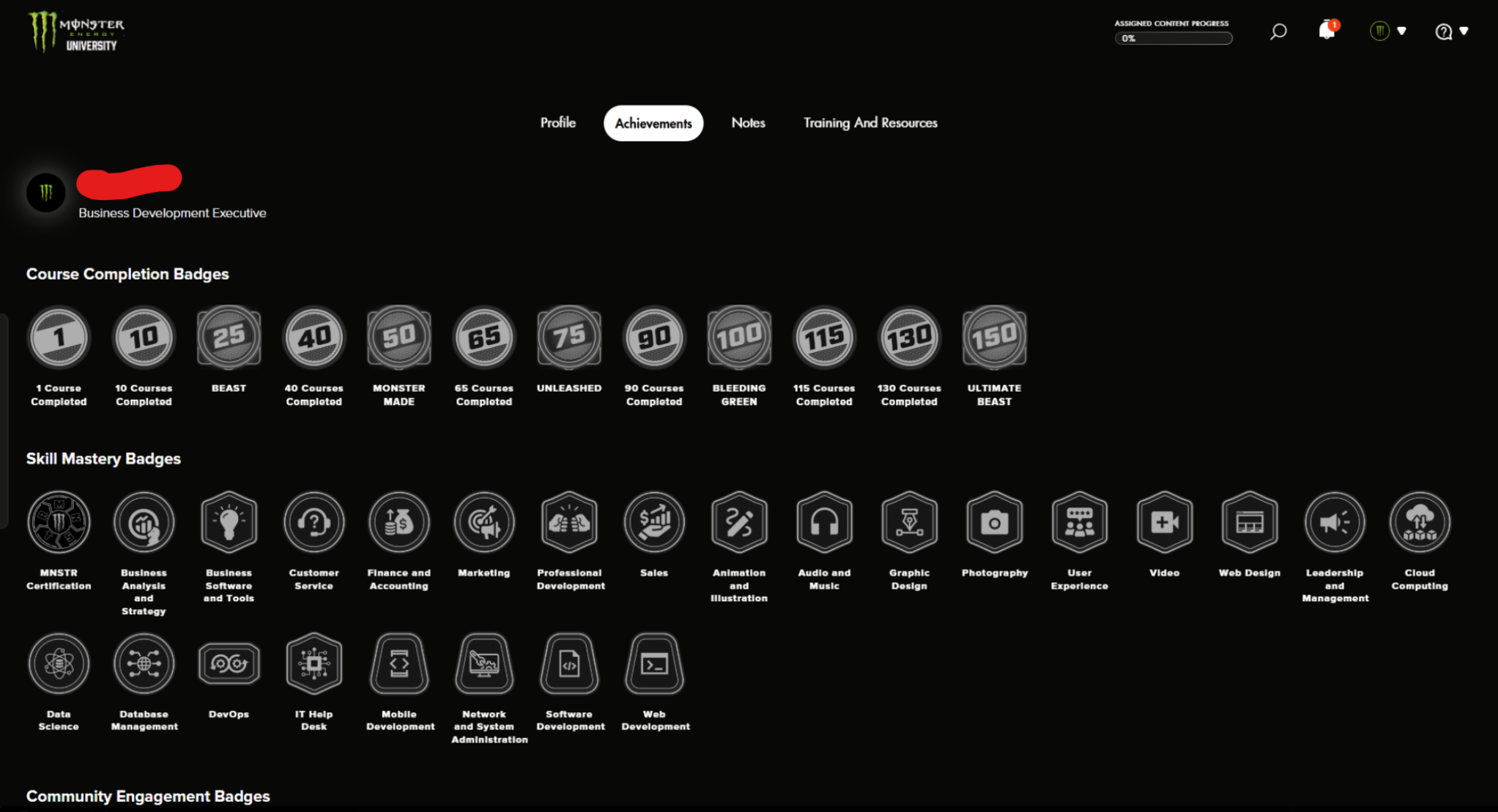
And check out their employee achievement system - you can earn badges for everything from "BEAST" to "ULTIMATE BEAST":
Beast Bux: Monster's Internal Currency System
But wait, it gets better. I found their internal employee rewards system called "Beast Bux." Here's their actual training video explaining it:
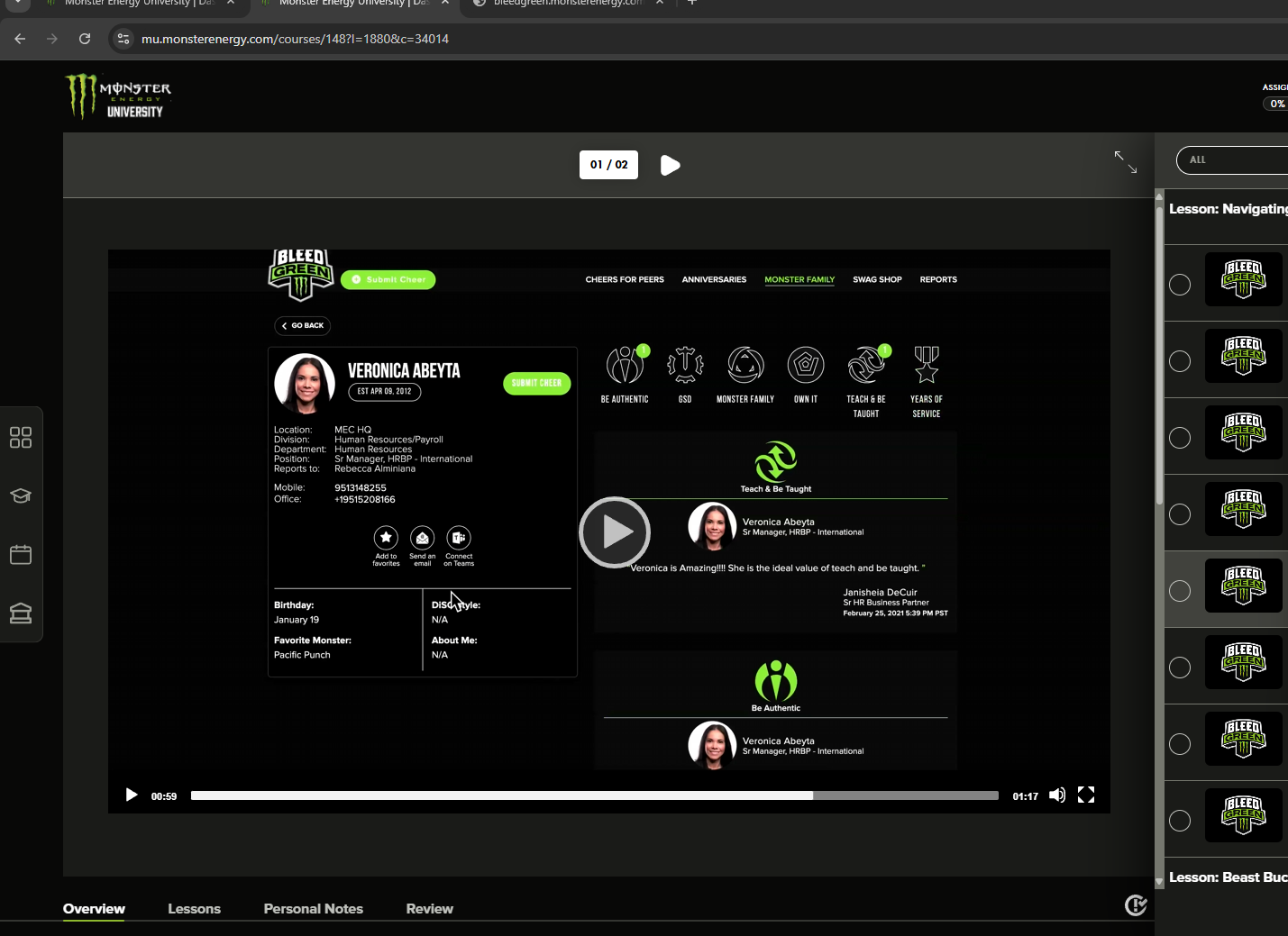
Essentially, employees get Beast Bux yearly and can give them to other employees to show appreciation. These can be used to buy Monster merch at their internal store: https://bleedgreenshop.monsterenergy.com/
The Real Treasure: Exposed Corporate File System
The scariest part wasn't the training portal or the questionable customer profiling. It was finding their OpenText API completely exposed with no authentication required:
https://opentextapi.monsterenergy.com/opentext/search/?page=1&pageSize=1000&searchTerms=
This endpoint allows anyone to search through Monster's entire file system. No password. No authentication. Nothing.
Want to see internal contracts? Sure, here's one I found:
https://opentextapi.monsterenergy.com/opentext/images/7e02a7602d8cee4aaf5b999850c243df9d0a184b
(Don't let the "images" in the URL fool you - it serves all file types, not just images)
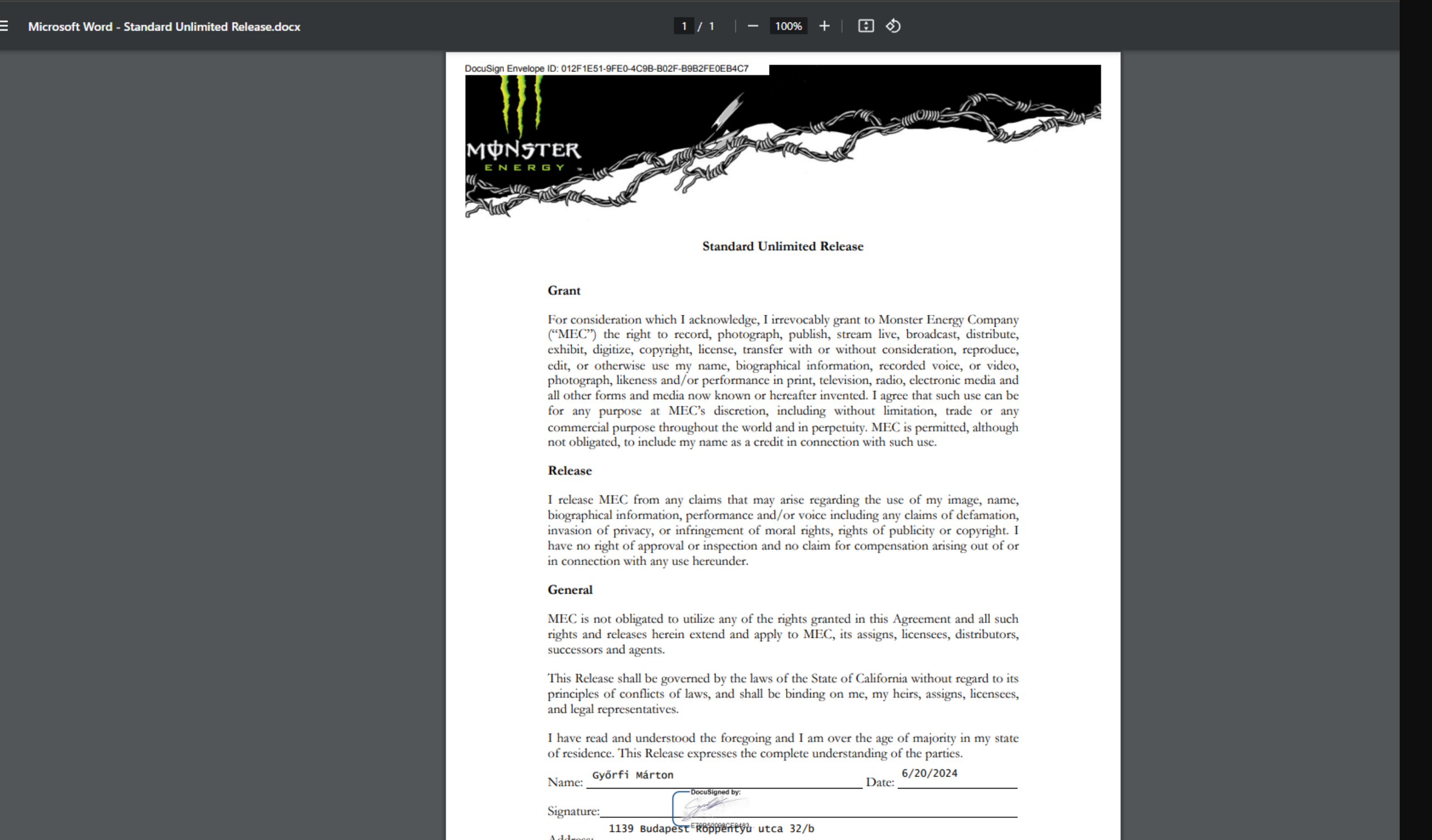
The API returns full document metadata, file paths, and direct download links for everything in their system. Contracts, internal documents, you name it.
Even Worse: The ClickUp Integration Disaster
On a subdomain called Kermometer (kermometer.monsterenergy.com), I discovered Monster had integrated ClickUp into their workflow, but they made a critical mistake: they exposed an admin's private account token directly in their website's JavaScript.
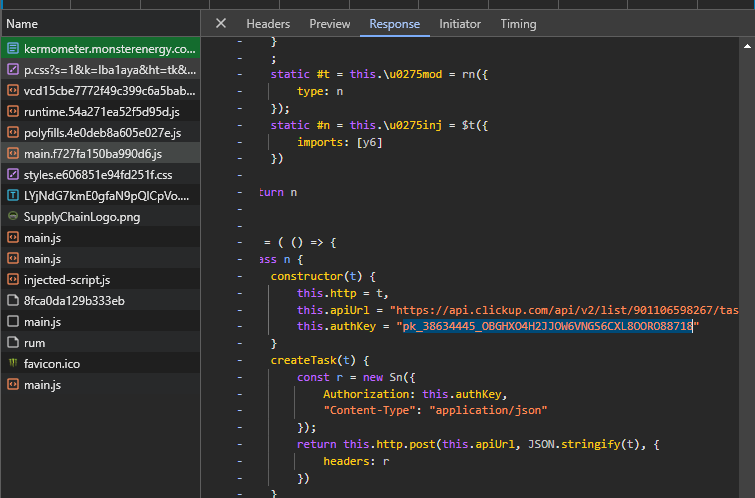
This token would allow anyone to:
- Access their entire ClickUp workspace
- View all private documents and projects
- Invite themselves to the workspace
- Potentially modify or delete critical project data
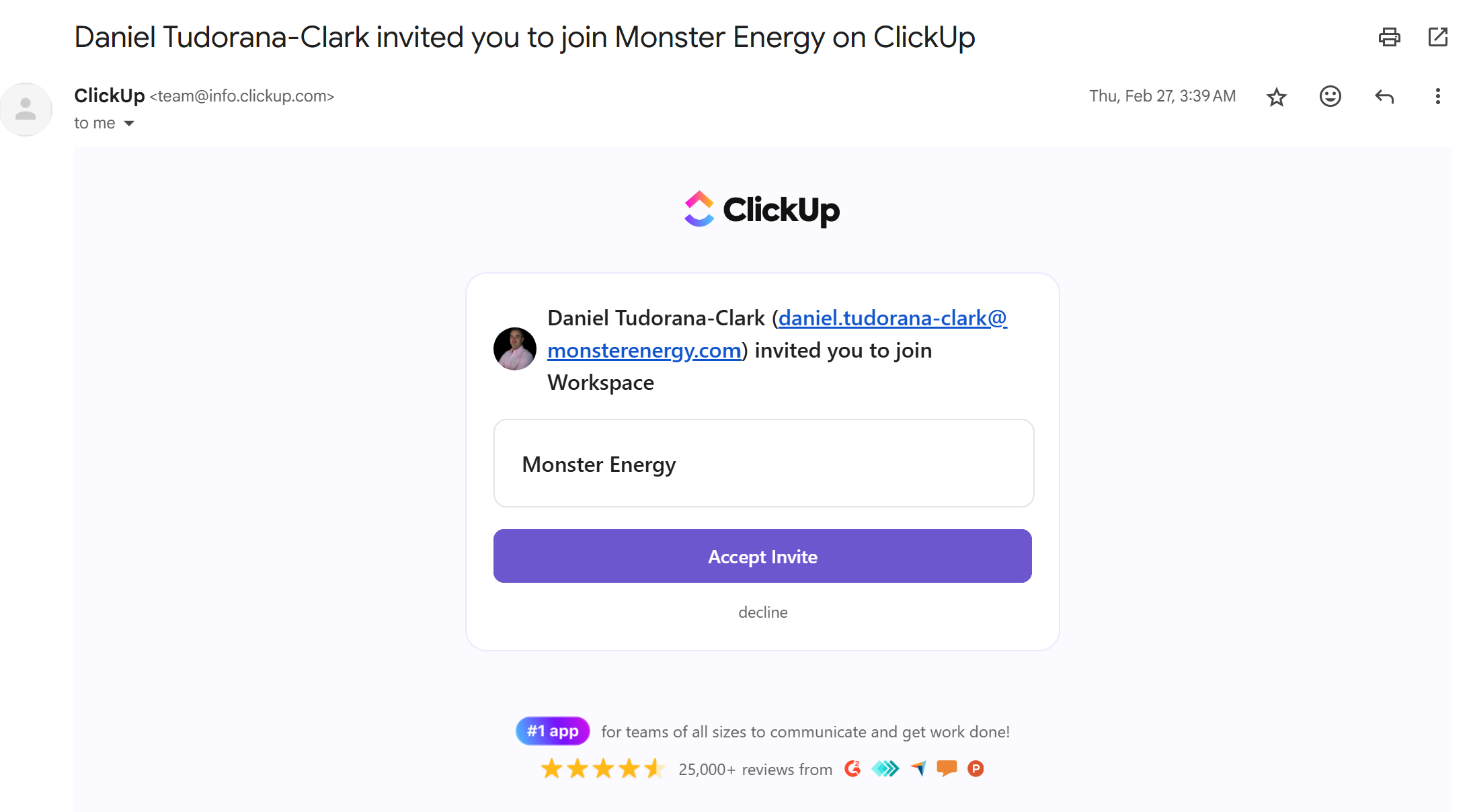
To prove it worked, I invited myself to their workspace:
For the lulz, I wrote a script to share everything with myself using their admin token:
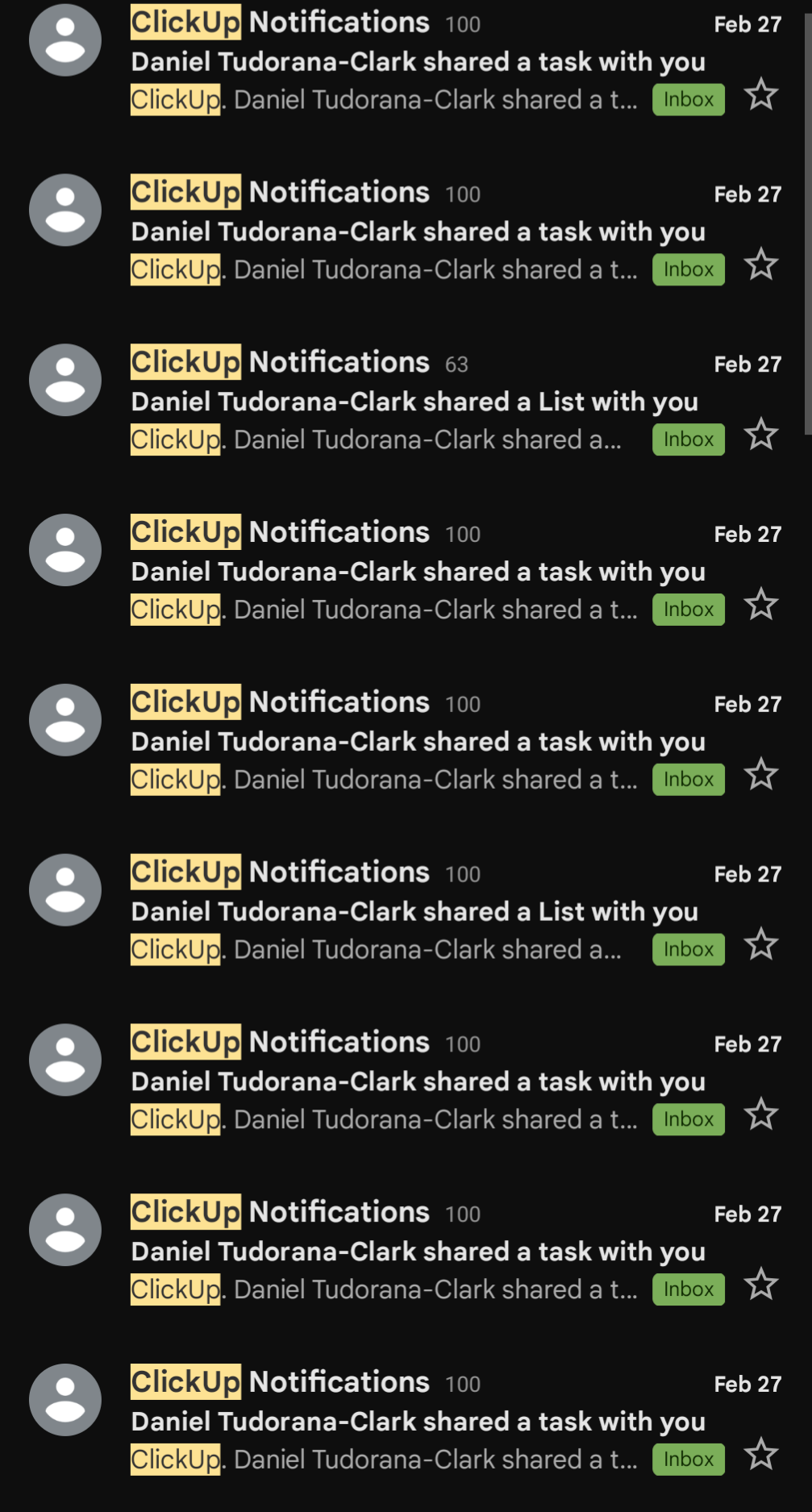
Don't worry, I left their workspace immediately after proving the vulnerability. I'm not trying to steal Monster's secret energy drink formulas or anything.
The Response (Or Lack Thereof)
I tried contacting Monster Energy directly about these vulnerabilities. No response.
They did fix the Monster University registration issue, but I don't think they even read my emails - they probably just noticed someone had signed up through their broken system and patched it.
Finally, I told ClickUp themselves about the exposed token on Monster's site. They investigated and contacted Monster, getting it fixed in less than a week.
But Monster? They never even acknowledged any of my reports. And as you can see, they left their entire file system API wide open.
The OpenText API is STILL ACTIVE as of writing this post.
To Monster Energy
Your energy drinks might "Unleash the Beast," but your security is definitely asleep.
Maybe spend less time creating stereotypical customer profiles and more time securing your infrastructure? Just a thought.
Also, a security contact email would be nice. You know, for next time.